Hello Folks,

My self Sanket Sherkhane , an active security researcher, bug bounty hunter and also an aspiring ethical hacker with pursuing CSc. This is my first writeup, so please bear if you find any typos or grammatical mistakes. I actually had never thought of writing a blog over my researches , but this was quite interesting and new type of finding to me till date. Also this bug was discovered accidentally.!
Summary:
So after testing on many other domains, I thought to hunt on Apple domain(yes, you read it right! its apple domain. As it was an accidental bug, read further to know how I ended up discovering the bug in google domain), and also I came up with successful finding in apple, which was low hanging fruit. I reported and I was waiting for reply from apple. After some three days, I got a mail from apple asking me to reproduce the same issue with curl and traceroute tools and provide them a POC(Proof-Of-Concept) of output by the tools. So I ran the tools as they said and was able to reproduce the same with tools , soon I copied the outputs and pasted in a text file which was containing the http request with HTML tags in it. and now
Here comes the real catch for accidental find !
I uploaded the same file to google drive normally and I observed that the thumbnail of a text file was rendering the html tags from the file. Now I was like👇,
With that said, lets get started,
Soon as I found this, I immediately created an text file adding text with some basic HTML tags like markdowns. ex: <h1>,<i>,bg-color; just like a common practice. And uploaded the text files to google drive and surprisingly, I was able to see the html tags executed on thumbnail .
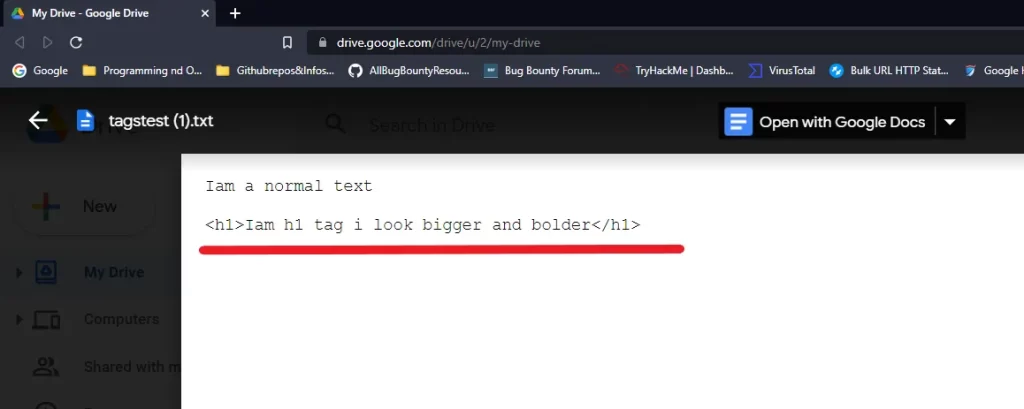

Another Example:
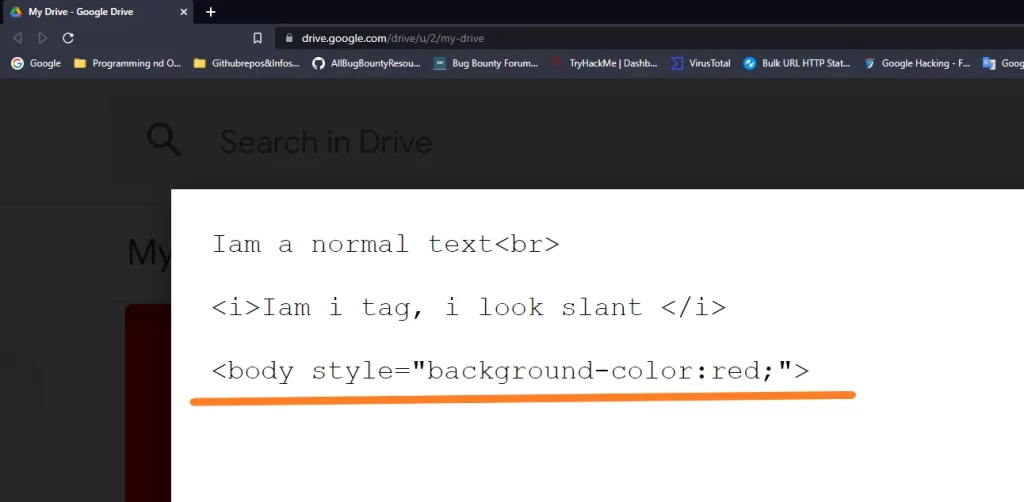
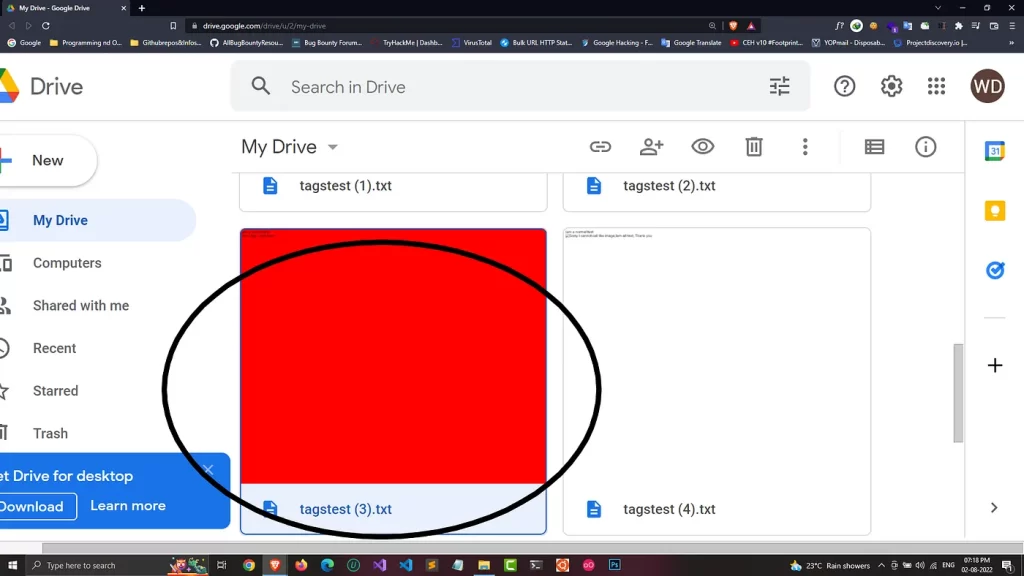
So after seeing all such behaviours , I was like,

Soon I recorded the POC video , wrote the report, attached POC and submitted it to google and was holding back for their reply . The next day I opened my mail, with no surprise, I got email from google & guess what!! No no, report didn’t get triaged , It was marked Intended behaviour :((
Reason for intended behave: Even the issue was valid, there was no harm for product coz, the HTML tags were rendering on the server side inside the sandboxed environment :))
Google’s Reply👇
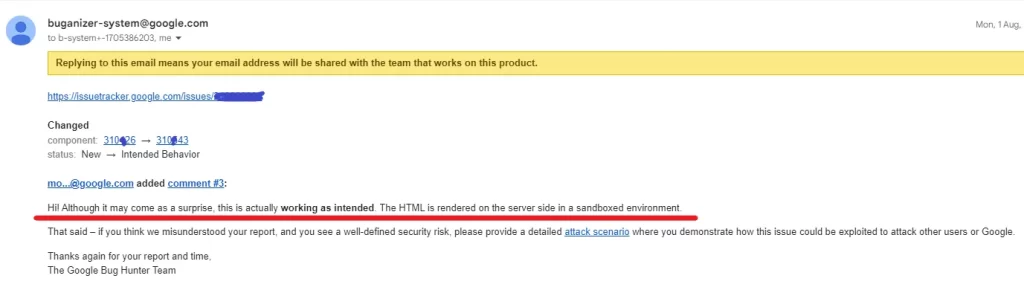
As always , it didn’t surprised me with the reply 🙁 !

POC[Video]: https://youtu.be/O3HOKBfhmws
Anyways, I didn’t worry much about this even though it was not rewarded/triaged. coz I was much happy with my finding. The way I discovered the bug ,the company which I found a bug in was “GOOGLE”, the name itself gives me proudness. The way of thinking was out of box here and it was the best finding for me
Never mind even if its a feature too! what matters is, how I discovered 🙂
…..
Timeline:
Reported: 31 July 2022 4:04 am
Marked Intended: 1 Aug 2022 7:20pm
…..
SO that’s it for the blog guys, Thank you so much for reading till here and spending your time on my write up. Hope you found it useful and read something new.!
Any suggestions or feedbacks are appreciated . Any queries ? feel free to DM on LinkedIn.
LinkedIn Profile: https://www.linkedin.com/in/sanket-sherkhane-955ab5204/
- *Take away**: Observe each and every minute(small) things/features on the target very carefully. Sometimes you may end up in finding valid and interesting bugs.
See you in an another interesting finding. Till then Peace out✌👋


Author
Mr. Sanket Sherkhane
Security Researcher | Bug Hunter | Ethical Hacker | WAPT

